
Online Payment Security: A Guide for Businesses
Online Payment Security is crucial for business websites and the customers who depend on them to make purchases. Specifically, businesses need to prioritize securing the online payment gateways on their sites, as it plays a vital role in ensuring secure eCommerce transactions.
With the increasing popularity of online transactions, businesses must invest in strong security measures. Of course, loads of benefits come with it.
The Importance of Online Payment Security
Online payments come with numerous benefits and opportunities, especially for businesses. For instance, various people pay bills or subscription charges online due to its convenience. Additionally, billions of shoppers online enjoy purchasing goods and services.
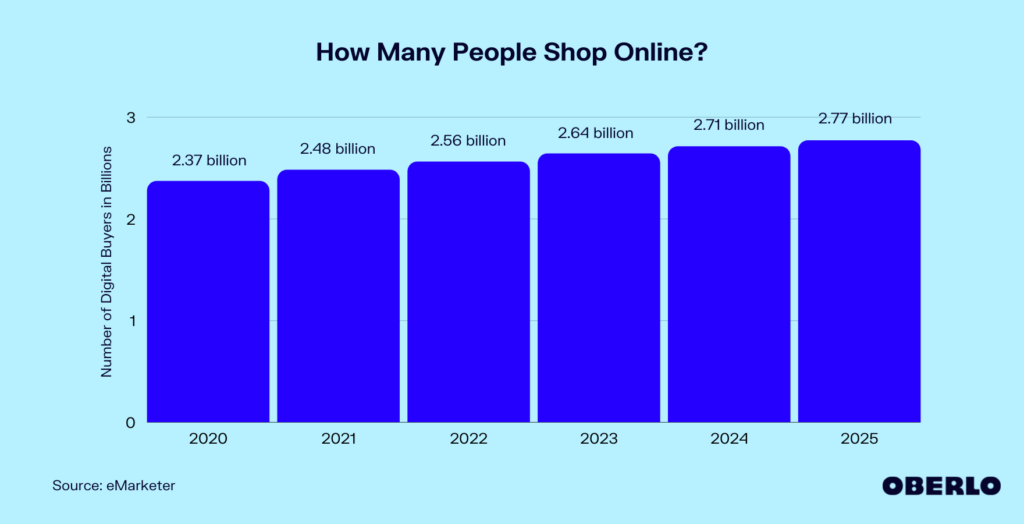
Source: Oberlo.
Here is a list of reasons why payment security is critical for businesses:
- Protects financial assets;
- Protects intellectual property;
- Reduces chargebacks;
- Preserves consumer trust;
- Meets customer expectations;
- Builds long-term relationships;
- Ensures regulatory compliance;
- Supports business growth;
- Enhances operational efficiency;
- Gives the business a competitive advantage;
- Prevents fraudulent activity, and
- Prevents data breaches.
However, although it has various benefits, online payment comes with risks and challenges.
Common Payment Security Threats
Threats to Online Payment Security pose significant risks to individuals and businesses. After all, they can result in adverse outcomes, such as financial loss, data loss, damaged reputations, and more.
Thus, you should secure online payments by staying alert and adopting best practices. Lastly, you must invest in cybersecurity measures. Proactive security can protect sensitive payment info and prevent financial loss and reputational damage.
Here are some of the most common Online Payment Security threats to avoid:
Phishing Attacks
Phishing is a cyberattack where fraudsters impersonate trusted entities to steal sensitive information. Attackers create scams or use fraudulent messages or websites that appear genuine to trick unsuspecting people.
Check Out Our Website Security Solutions Here!
Recent phishing attacks are more sophisticated and targeted. For example, spear phishing attacks trick high-level personnel into granting access or even authorizing payments.
Here are a few solutions organizations can implement when dealing with phishing scams:
- Implementing email filtering solutions and authentication protocols.
- Conducting regular employee awareness training and simulations on phishing attacks.
- Enabling Multi-Factor Authentication (MFA) for systems and applications.
- Regularly apply security updates and patches to software, email clients, browsers, and operating systems.
- Install robust endpoint security solutions to detect and block malicious activity.
- Use URL Scanning and Email Authentication tools to detect links or phishing attempts in emails.
- Running customer education campaigns, such as info drives or posting advisories.

Data Breaches
Breaches are unauthorized access to a system or database containing sensitive information. In addition to hacking or malware, breaches often occur due to weak security and insider threats.

Source: Embroker Insurance Services LLC.
Ultimately, data breaches can result in the following:
- Financial loss;
- Legal liabilities;
- Damage to your reputation, and
- Customer trust issues.
You can manage a breach by complying with Data Privacy Laws and limiting access to sensitive data to personnel needing it. Here are other ways you can manage data breaches:
- Activating your Incident Response Team once you discover a breach.
- Isolating and containing the breach.
- Notifying and cooperating with the appropriate authorities.
- Communicating with internal stakeholders (employees) and external ones (customers or the public).
- Conduct a thorough analysis concerning the data breach’s origin.
- Then, patch security vulnerabilities and remediate weaknesses.
Malware and Ransomware
Malware is harmful software that damages or accesses unauthorized computer systems. On the other hand, ransomware encrypts data and demands a ransom for decryption. These two can be delivered through email, compromised websites, or downloads.
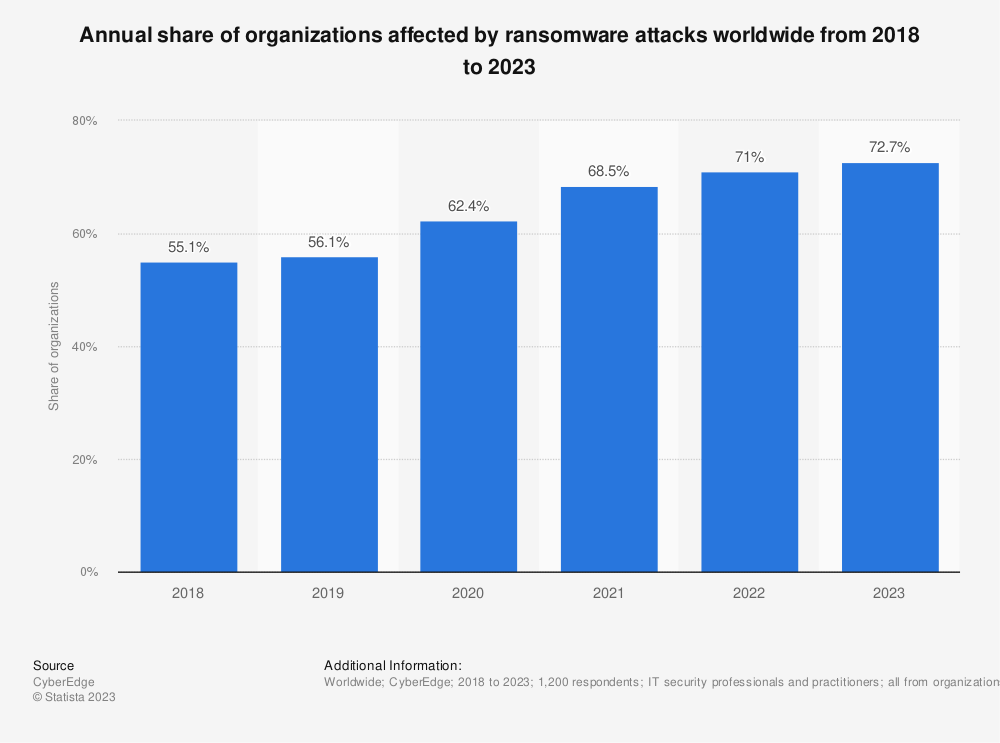
Source: Statista.
Malicious individuals can access sensitive data and passwords with advanced malware. Concerningly, it has evolved into sophisticated forms that can accomplish the following:
- Track keystrokes;
- Learn passwords;
- Infiltrate devices’ cameras and microphones; or
- Scrape browsing history.
Secure Payment Alternatives for Businesses
Payment gateways encrypt and process online payments. Thus, secure gateways are essential for safeguarding payment data. A secure payment system protects sensitive financial data, allowing you to gain and foster customer trust.
Businesses must integrate essential components, have layered security, and, most importantly, use a trustworthy and Secure Payment Gateway.
The Most Secure Online Payment Method
The most secure online payment method depends on your needs and preferences. Secure payment methods safeguard sensitive financial information and ensure safe transactions.
Thus, organizations must protect their financial information. More importantly, they can utilize payment methods incorporating various security features, including the critical elements of Online Payment Security. For example, encryption, tokenization, and authentication measures can protect financial data and prevent fraud.
Here are some generally Secure Online Payment methods:
- PayPal
- Mobile wallet services like Apple Pay and Google Pay
- Online bank transfers
- Online banking bill pay
- Third-party payment processors
Interested in Web Design and Development Services?
Contact Us Now!
PayPal
PayPal is an online payment service that acts as an intermediary between two users or a buyer and seller. Also, users link their bank accounts or cards to their PayPal accounts, further securing the payment gateway.
Mobile Wallet Services (Apple Pay and Google Pay)
With mobile wallet services, payments are made by tapping or using biometric authentication. This payment method lets users securely store debit card information on their mobile devices. Additionally, these services utilize tokenization to protect sensitive card data!
Bank Transfers
Of course, online transfers involve moving money from one bank account to another. Though it’s secure, customers must still share their bank account information with the recipient. Thus, the recipients must be trustworthy and verified to ensure the security of the transactions.
Online Banking Bill-Pay
Online banking bill-pay services primarily enable users to pay bills. Additionally, you can use it to make payments to individuals or businesses and schedule recurring payments through your bank’s online portal. Often, these services are secured with multi-factor authentication and encryption to safeguard financial data.
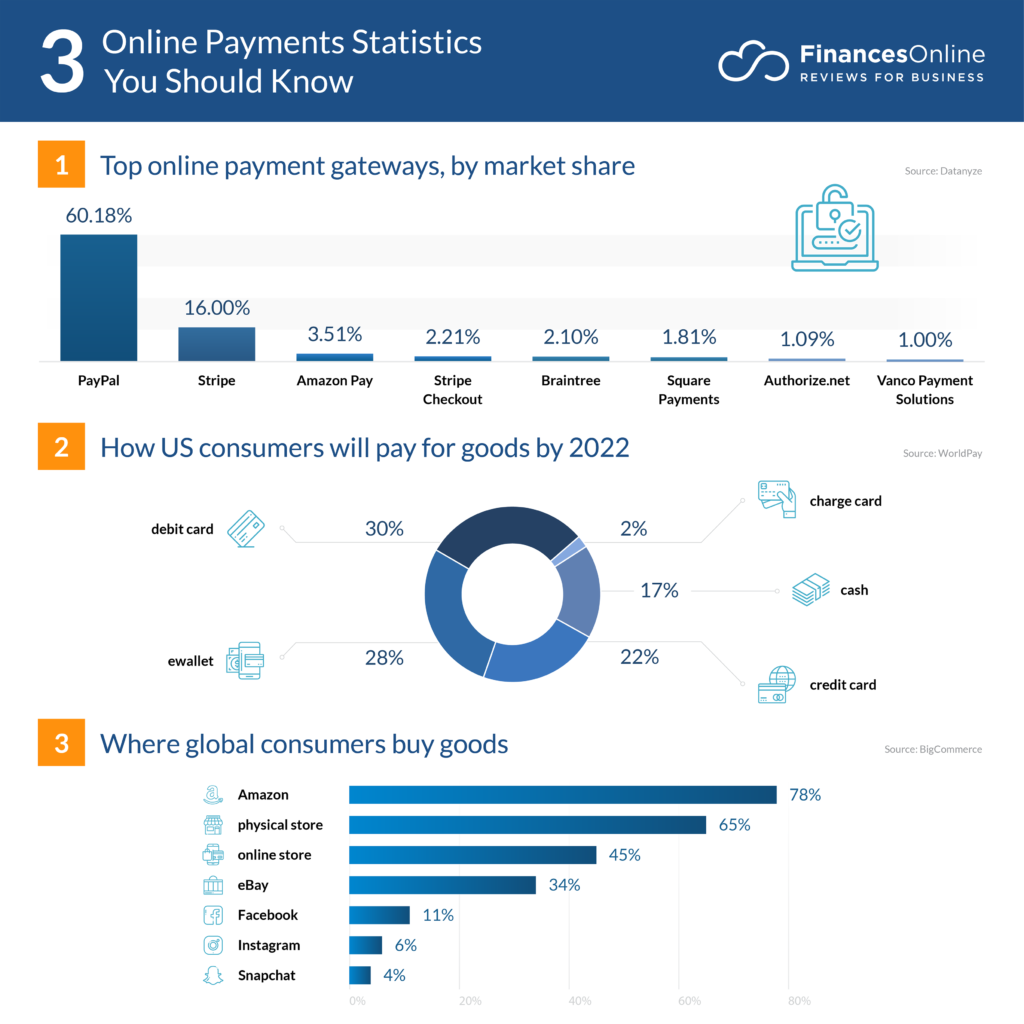
Source: FinancesOnline.
Secure Third-Party Payment Processors
Third-party payment processors offer businesses a secure way to handle business operations, like processing online payments. These processors are responsible for payment security and securely handle cardholder data. Also, it ensures compliance with industry standards, such as PCI DSS.
But, despite their many benefits, entrusting sensitive information to such processors can be a security risk. So, you must thoroughly evaluate and select third-party service providers with a proven security track record. The ideal processors can safeguard sensitive information and maintain customer trust.
Remediations Against Attacks
Since many rely on digital payment processing, ensuring the security of customer payments has become a top priority. There are a fair amount of risks associated with online payment processing. Also, various threats and attacks can leave individuals and businesses vulnerable to fraud and data breaches.
Thus, you must safeguard against potential security weaknesses and strengthen the overall security of online payments. To protect against these threats, here are the security measures you must implement:
Data Encryption
Strong encryption algorithms protect sensitive data like customers’ personal details and credit card information, whether in transit or at rest.
Data encryption secures customer information using Secure Sockets Layer and Transport Layer Security. SSL and TLS protocols will encrypt data transmitted between a user’s browser and a server. As a result, it prevents network eavesdropping and Man-in-the-Middle attacks.
However, organizations shouldn’t just stop at encryption because it’s not a complete solution. So, it should be part of a robust and comprehensive security strategy.
In addition, PCI regulations prohibit using encryption to remove data from PCI scope.
Tokenization
In tokenization, you replace payment information with tokens, random values that seem to have no meaningful relationship to sensitive data.
Two-Factor Authentication (2FA)
This authentication type requires two forms of identification to complete a transaction. For instance, you may need a password and a code from a secondary device. For greater security, you must implement 2FA for online user accounts and transaction verification.
Regulations Compliance
Businesses must comply with regulations and standards to ensure secure online payments, including:
- Payment Card Industry Data Security Standard. This security standard is the primary regulation for businesses that handle credit card information.
- The General Data Protection Regulation protects EU citizens’ privacy and data. Thus, organizations processing EU residents’ data must comply with the GDPR.
Web Application Firewall (WAF)
Web Application Firewalls filter and block malicious traffic. Also, they protect against common web application attacks, including the following:
- Structured Query Language (SQL) injection;
- Cross-Site Scripting (XSS), and
- Cross-Site Request Forgery (CSRF).
Regular Software and Plugin Updates
Outdated software is vulnerable to attacks, so you must keep up with the latest security patches. You must patch whatever software, platforms, and plugins you’re currently using.
Patching is indispensable for all organizations. However, patches must also be implemented across various operating systems, applications, and network infrastructure. Regular and comprehensive patching can safeguard your systems against cyber threats.
Strong Password Policies
You must have a strong password policy and utilize unique passwords that are hard to guess. Additionally, you should make it a habit to regularly change passwords.
Regular Security Audits
Audits are critical for identifying vulnerabilities in payment systems. Thus, you must conduct regular audits and penetration testing and promptly fix any vulnerabilities.
Monitoring and Fraud Detection
In addition to finding vulnerabilities within the system, you must monitor payments in real-time to identify unusual or suspicious payment transactions. After all, abnormal patterns can be indicative of fraud or attacks.
On the other hand, you must also implement fraud detection systems that flag potentially fraudulent transactions. Through machine learning and pattern recognition, these systems identify unusual transactions.
Customer Education
You can teach customers about safe online payment practices, like recognizing phishing attempts and ways to protect their payment data.
In addition, businesses can use it to build trust with customers through transparency. This can be achieved through educational resources, clear privacy policies, secure payment processing, and more!
Incident Response Plan
Organizations, in particular, should develop an incident response plan to quickly address security breaches. For instance, you must define roles and responsibilities for responding to potential attacks.
One key component of incident responses is having data backups. Thus, you should back up transaction and customer data regularly, ensuring you can recover from data loss. This loss may occur due to attacks or system failure.
Final Thoughts
Making online payments secure is crucial for businesses for various reasons. Secure payment gateways are essential for eCommerce transactions. Online payments offer convenience for businesses, such as protecting financial assets and preventing fraud and data breaches. But they also come with risks.
Common security threats include phishing attacks, data breaches, malware, and ransomware. There are plenty of Secure Online Payment Methods, including the following:
- PayPal
- Mobile wallet services
- Bank transfers
- Online banking bill pay
- Third-party payment processors
You can protect your customers’ financial information by learning about payment security. Not only that, but you must be vigilant for the signs of payment gateway security and then implement security measures and protocols. Additionally, the following reduce security risks and protect sensitive payment information:
- Data encryption
- Tokenization
- Two-factor authentication
- Regulations compliance
- Web Application Firewall
- Regular software and plugin updates
- Strong password policies
- Regular security audits
- Monitoring and fraud detection
- Customer education
- Incident response plan
Count on eCommerce Website Design and Development Services to help you protect your business and its customers!














Comment 0